What is Azure Active Directory Seamless Single Sign On?
.png?width=600&name=What%20is%20Azure%20Active%20Directory%20Seamless%20Single%20Sign-on_%20(1).png)
We’re all dealing with many usernames and passwords in our everyday life, right? Today I’d like to talk about an authentication feature within Azure Active Directory that can help you with easier, faster access.
Azure Active Directory Seamless Single Sign-on (Azure AD Seamless SSO) automatically signs users in when they are on their corporate devices connected to their corporate network. When this is enabled, users don’t have to type their passwords, or even their username, to sign in to Azure Active Directory.
This feature provides users with easy access to cloud-based applications without needing any additional on premises components. First let’s look at how this is set up:
- SSO is enabled used Azure AD Connect. The following steps will occur while enabling this feature:
- A computer account representing Azure AD is created in your on premises Active Directory in each AD forest.
- The computer account Kerberos decryption key is shared securely with Azure AD and then 2 Kerberos service principal names (SPNs) are created to represent 2 URLs that are used during Azure AD sign-on.
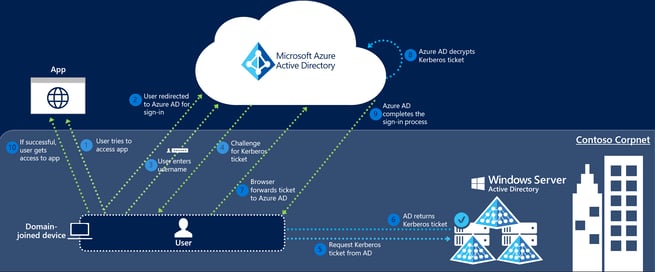
- When doing authentication from a web browser for a web app, essentially a user navigates to a website and signs into Azure AD (see below).
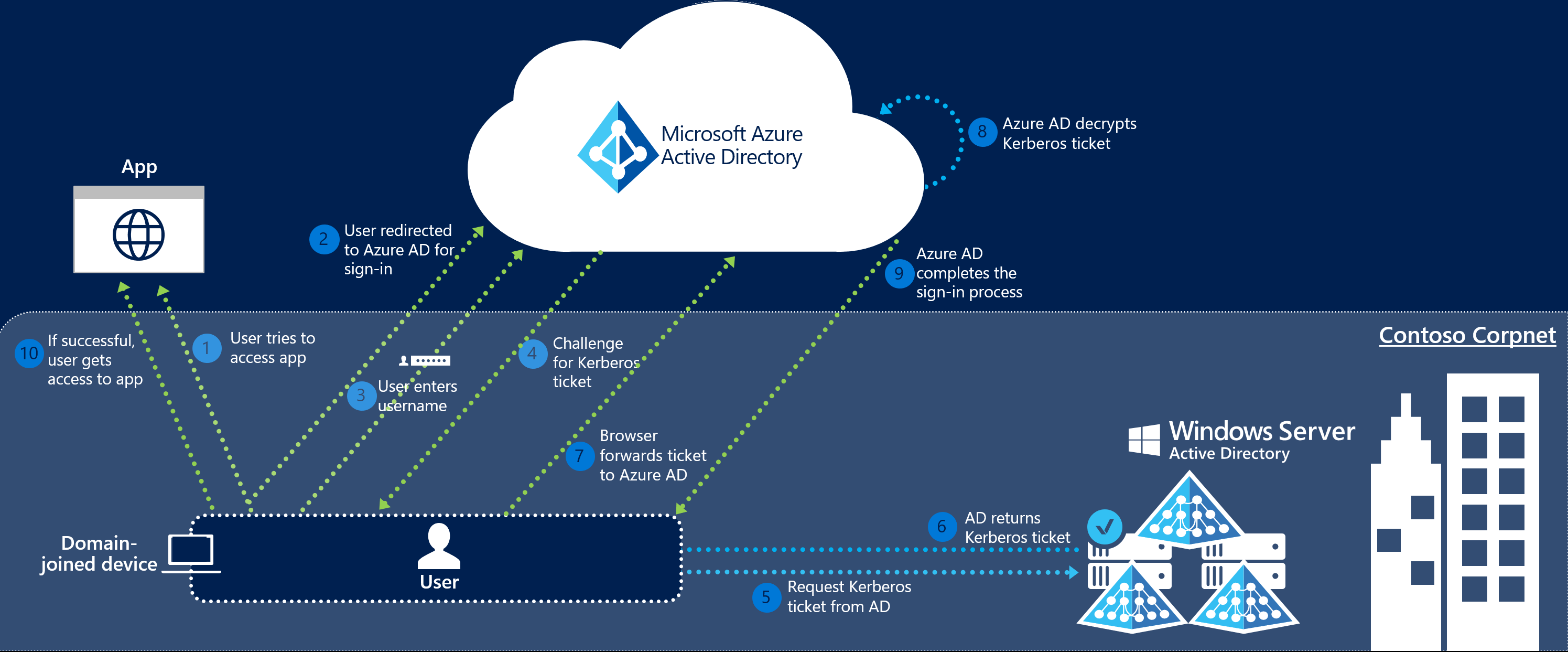
- Azure AD sends a Kerberos requests to on premises AD and on premises AD looks for an account related to the device you’re signing in on and a user account. If authorized, you get access.
- For a native client, like Outlook for instance, the process is a bit different (see below).
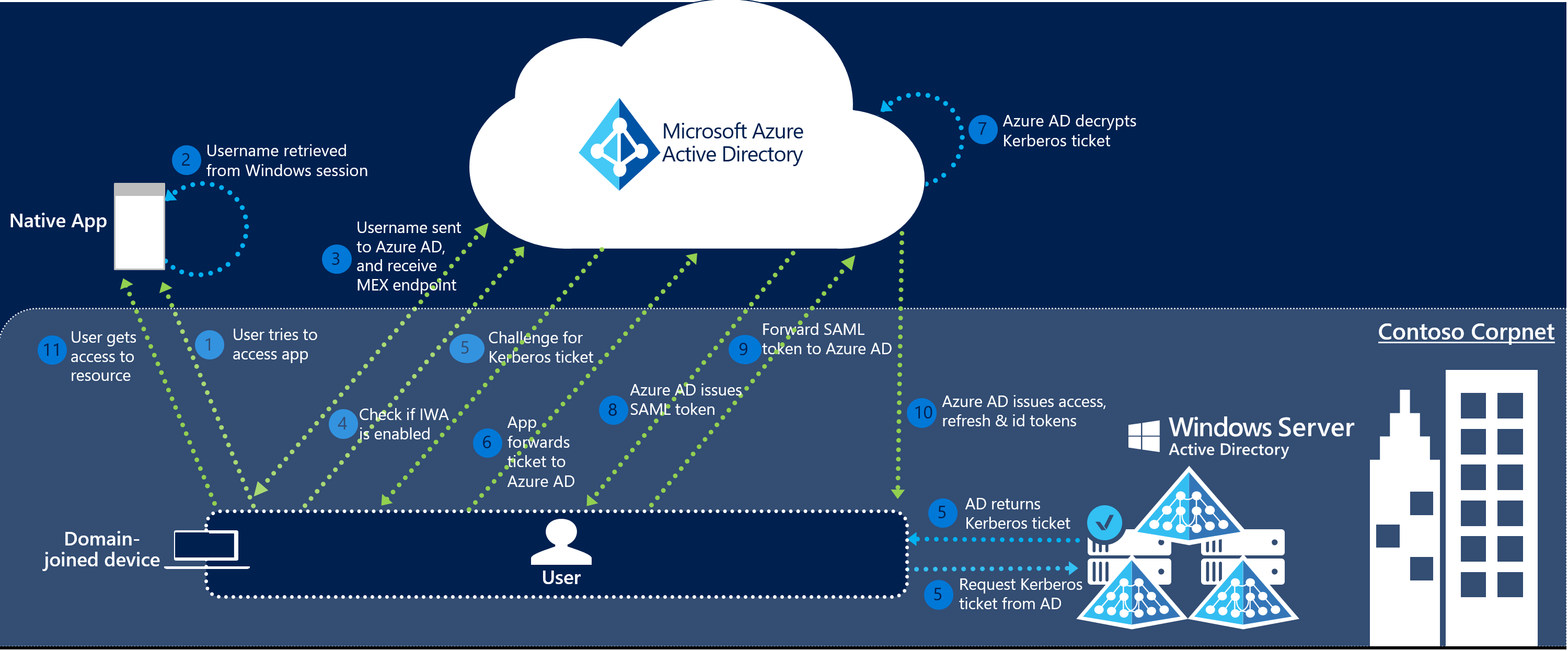
- Here, the request is made from the device you’re using and authenticated off Azure AD, issuing a Kerberos ticket when it is successful.
- When that ticket is authenticated off Azure AD and approved, a SAML token is sent to the app. Then it gets sent back to AAD for OAuth-2 authentication.
- Once all that checks out, access is granted.
Now let’s talk about the benefits. First, it’s a much better user experience. Users are automatically signed in both on premises and cloud-based applications using their built-in authentication, so there’s no need for users to repeatedly reenter their passwords.
It’s also easy to deploy and administer. There are no additional components needed on premises; it synchronizes your Azure Active Directory to your AD. Plus it works with any method of cloud authentication using password hash synchronization or pass through authentication.
Additionally, it can be rolled out to only some or all of your users by using group policy. So, this is a great way to allow users to have multiple authentications into multiple websites and applications using only one authentication tool. This will minimize the amount of administration required to set up those users once it’s in place. And it should reduce the number of password resets for your help desk team or whomever oversees that.
If you’re interested in learning more about identity management in Azure, Azure security or anything about the Azure data platform, we are the people to talk to. Click the link below or contact us – we’re here to help you take your business from good to great with Microsoft Azure.
Sign-up now and get instant access

ABOUT THE AUTHOR
Free Trial
On-demand learning
Most Recent
private training






-1.png)
Leave a comment